|
|
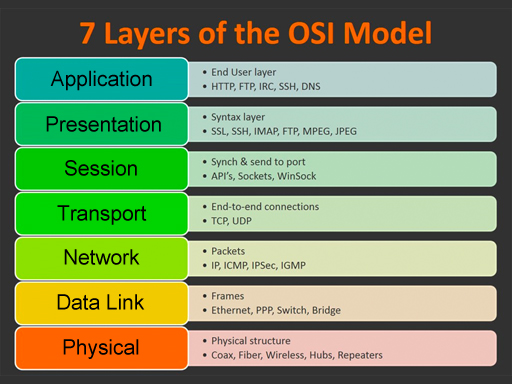
| This glossary uses network terms from the OSI model. Click on one of the categories on the left or on the image below. Click the View All link to see all terms. Use the alphabet to jump to that letter. Some of the terms could be used on multiple layers, but they are grouped in the most common layer. |
All Terms
View All
|
|
|
#
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
|
#
3G |
| The second generation of digital cellular communications technology characterized by minimum speeds of hundreds of kbps and tens of Mbps at the high end. Providers of 3G service continue to use circuit switching—as was done in the early voice-only 2G technologies—to make voice calls. (Physical Layer) Top |
|
|
4G |
| A digital cellular communications technology that ranges in speed from 100Mbps to 1Gbps and is based entirely on a packet-switched IP network. With 4G networks, voice is implemented as voice over IP (VoIP). (Physical Layer) Top |
|
|
5G |
| An emerging digital cellular communications technology exceeding the specifications of earlier generations of mobile communication. As of early 2017, the final touches had not been agreed upon by the International Telecommunication Union (Physical Layer) Top |
|
|
802.11 |
| The IEEE standard for wireless LAN (WLAN) implementation. The IEEE 802.11 standard includes a number of notable specifications including 802.11a: 54Mbps maximum speed, 5GHz UNII frequency range; 802.11b: 11Mbps, 2.4GHz ISM frequency range; 802.11g: 54Mbps, 2.4GHz; 802.11n: 600Mbps, 2.4GHz and 5GHz; 802.11ac: 1300Mbps, 5GHz. (Data Link Layer) Top |
|
|
802.1X |
| A port-based authentication protocol used on wired and wireless LAN access devices. The IEEE 802.1X standard is employed on Layer-2 switches and wireless access points (WAP) to require systems connected to interfaces on such devices to submit credentials—username and password, for instance—before network access is granted. (Data Link Layer) Top |
|
|
A
Analog signal |
| A communications waveform that is analogous to the source of the signal. Often represented as a sine wave, analog signals must be transmitted all the way to the target exactly as produced in order to provide a precise representation at the receiving end. Due to attenuation and external noise influence, this goal is largely unattainable. Filters and shields can be implemented with analog signals to somewhat improve the quality of the received signal. (Physical Layer) Top |
|
|
Antenna |
| A device that converts between radio waves and electrical current. Antennas are used in various circuits and systems to transmit and receive wireless signals in the form of radio frequency energy. (Physical Layer) Top |
|
|
APIs |
| Stands for "Application Programming Interface." An API is a set of commands, functions, protocols, and objects that programmers can use to create software or interact with an external system. It provides developers with standard commands for performing common operations so they do not have to write the code from scratch. (Session Layer) Top |
|
|
ARP (Address Resolution Protocol) |
| The protocol responsible for associating a logical address (often from a Layer-3 protocol) with a physical address (often from a Layer-2 protocol). ARP is most often employed to broadcast a request on the local IP subnet for the Ethernet MAC (Media Access Control) address of a specific host when its corresponding IP address is already known. (Transport Layer) Top |
|
|
ASCII (American Standard Code for Information Interchange) |
| The character set used in the Disk Operating System (DOS) of the original IBM Personal Computer (IBM/PC) line. A character set is a code that assigns one of the binary permutations in the character set to each of the characters available to text-based applications running on the operating system. ASCII is a 7-bit code while Extended ASCII is an 8-bit code. The result is a set of 128 characters and 256 characters, respectively. (Presentation Layer) Top |
|
|
Asynchronous communication |
| A data communication method between two devices that is achieved without using a common clock signal. Other characteristics of asynchronous communication include periods of no communication at all and the ability to vary the rate of bit transmission. The classic RS-232 serial port included with most legacy computer systems is a well-known interface that employs asynchronous communication. (Data Link Layer) Top |
|
|
Attenuation |
| Loss of signal strength along a communications pathway. Attenuation is often measured in decibels (dB) and results from natural resistance in the wired or wireless channel and from other environmental factors. (Physical Layer) Top |
|
|
B
Backbone |
| A media pathway of higher capacity than those used to connect end devices to the network. Backbones are often deployed to interconnect equipment rooms or cross-connection spaces containing concentrating devices used to offer connectivity to end devices in a star-wired infrastructure. Backbones simultaneously carry traffic for multiple end devices. (Physical Layer) Top |
|
|
Bandwidth |
| In analog or digital communication, the channel occupied by the carrier and measured as the difference in hertz (Hz) between the highest and lowest frequencies in the channel. (Data Link Layer) Top |
|
|
Baseband |
| A type of digital signaling that features the use of a single frequency or near-zero bandwidth to transmit a bitstream. Baseband signaling is used in Ethernet networks and is represented by “BASE” in the names of the various physical-layer technologies, such as 10BASE-T, 100BASE-TX, 1000BASE-T and 10GBASE-T. (Physical Layer) Top |
|
|
BGP (Border Gateway Protocol) |
| The exterior gateway routing protocol used to build the routing table of the commercial internet. BGP version 4 (BGP4) is the only exterior gateway protocol (EGP) in use today. Internet service providers (ISPs) use BGP to share external routes they learn from customers and other ISPs with one another. Propagating all routes among the ISPs of the internet enables all internet clients to access much of the internet’s sites and resources. (Transport Layer) Top |
|
|
Binary |
| Characterized by having two parts. A binary system is one that has two separate components. In electronics, binary can refer to the state of a circuit or memory cell, either on or off, present or not, “yes” or “no.” Scientists use the binary numbering system to mathematically represent and predict such circuits with two numerals—0 and 1—allowing for the creation and troubleshooting of individual components as well as entire systems. Popular usage of the term refers to the binary numbering system, which is one of only a few such systems (out of an infinite possibility of numbering systems) that humans commonly employ to describe the world around them. Octal (base-8), decimal (base-10) and hexadecimal (base-16) are the other three numbering systems that you can expect to deal with in the technology industry. (Physical Layer) Top |
|
|
Biometrics |
| A form of identification based on individual human traits. Literally “the measure of life,” the field of biometrics uses a variety of biological measurements in an attempt to differentiate one human from all others by using features such as fingerprints, palm prints, voice, handwriting, retina, iris and recognition of facial features. (Data Link Layer) Top |
|
|
Bit (b) |
| The basic unit of the binary numbering system. The word bit is a portmanteau of the term “binary digit.” Therefore, the word bit refers to one of the two numerals, 0 or 1, in the binary numbering system. The industry also supports using the word “bit” to represent a single position in a numeric value that is being expressed in binary, regardless of its bit-value. (Physical Layer) Top |
|
|
Bits per second (b/s or bps) |
| A unit of measure for the movement of data between devices and/or across a medium. Also known as “bitrate.” Almost all measures of data transmission speed are based on bps. (Physical Layer) Top |
|
|
Bridge |
| In Ethernet, a Layer-2 legacy networking device replaced almost completely by routers in modern networks. Bridges replaced Layer-1 repeaters for interconnecting separate network cable segments and featured the advantage of understanding MAC addresses and Ethernet frame boundaries, allowing for the ability to forward data, when appropriate, and block—or filter—data that is not meant for a different segment. Today, the industry uses the term bridge as a verb to refer to passing information transparently from one interface to another on the same device without that device being a destination or source during the transmission. (Data Link Layer) Top |
|
|
Broadband |
| A type of wide-bandwidth communications signaling that supports the transmission of data from multiple sources, including those of varying types, separated across the series of frequencies in the bandwidth. (Physical Layer) Top |
|
|
Buffer |
| A digital memory location used to reduce the loss of data or the variation in the rate of data transmission. Without data buffers, a receiving system must be prepared to process external data presented to its interfaces immediately. Buffers are instrumental in communications systems in which variations in delay, known as jitter, can adversely impact the quality or usability of the system. Without such a buffer, real-time traffic must be compressed, or the transmission system must have no perceivable delay. (Transport Layer) Top |
|
|
Byte (B) |
| The most basic collection of bits required by a transmission pathway. Earlier systems required eight bits be transmitted or operated upon simultaneously, so the legacy definition of bytes containing exactly eight bits endures today. However, it is correct to say that an x86-64 processor operates upon a 64-bit byte, which might confuse the vast preponderance of the technology community. It has become common to use the term “octet” to refer to a group of eight bits because it is impossible to dispute that the root of the word refers to the value eight. (Physical Layer) Top |
|
|
C
Channel Service Unit/Data Service Unit (CSU/DSU) |
| A data circuit-terminating equipment (DCE) form of customer premise equipment (CPE) used to connect enterprise networking devices to a synchronous digital network, such as a T1 circuit. (Physical Layer) Top |
|
|
Checksum |
| An error detection mechanism for data that is based on the data but is generally much smaller than the original data. The best checksum algorithms result in the generation of a substantially different checksum after a relatively small change in the data. Most checksums are used to discover undesired changes in the original data, but longer checksums can even be used to recover the original data that was changed. (Data Link Layer) Top |
|
|
Circuit-switched network |
| A telephony or wide area network (WAN) link that provides a temporary connection over a dedicated pathway through the service provider’s network core. (Network Layer) Top |
|
|
CLI (Command Line Interface) |
| A user interface (UI) characterized by a text-based individual command parser. Most modern operating systems have a CLI; for some operating systems, the CLI is the primary interface. The most common accompaniment to the CLI is the graphical user interface (GUI), with which a mouse or other pointing device is often used. (Application Layer) Top |
|
|
Cloud |
| A term stemming from the abstract concept that the same data and services are available from seemingly limitless points of access. Cloud computing is a potentially extensive infrastructure of such services and methods of access, whether supplied by a cloud provider or internally, as from an enterprise’s own data center. (Physical Layer) Top |
|
|
Coaxial cable |
| Also known as coax for short; a common form of copper cabling characterized by having two conductors: one being the core of the cable, which is surrounded by the other, a braided shield. This design results in the inner and outer conductors having a common axis of rotation, which creates a signal pathway that supports higher frequencies with less signal loss and with less susceptibility to outside interference. (Physical Layer) Top |
|
|
Codec |
| A portmanteau of coder/decoder; an algorithm or a device using such an algorithm for converting analog sounds to digital bit streams (coding) and back (decoding). Codecs are almost as numerous in their uses as in their types. One use for codecs is in converting voice into a digital bitstream for storage or transmission across a network. (Session Layer) Top |
|
|
Compression |
| The reduction of the amount of data that is transmitted or stored. Some compression algorithms build a dictionary of longer codes that have been replaced by shorter codes before transmission or storage. The receiving device or the retrieving application uses the dictionary to expand the compressed information into its original form. This is known as lossless compression. Lossless compression is ideal for absolute data, such as financial information in a spreadsheet that must not be misinterpreted. (Presentation Layer) Top |
|
|
Console |
| The input and output devices employed by the user in operating a user interface (UI). Commonly, a terminal is the combination of a keyboard, a mouse (optionally), and a monitor. Consoles allow users to interface with systems, such as computers, routers, and switches, to configure or control them. The term “console type” is often used to refer to the terminal type, such as VT-100, set in terminal emulation software—Putty, for instance—to match similar settings on the device being managed by the console. Devices called keyboard, video, mouse (KVM) switches can be used to switch among multiple systems, controlled one at a time by a single console. (Presentation Layer) Top |
|
|
Cookie |
| A piece of data stored on a user’s system by their web browser. Some cookies are helpful and welcome while others are unwelcome because they invade the privacy of the user. (Session Layer) Top |
|
|
D
Data |
| Any form of information that is used as input to a system or application for processing or that is produced as the output from a system or application. After the better part of a century of electronic data processing, data collection and analysis has entered an arena known as “big data.” The term big data analytics speaks to the capacity of modern computers to scour such vast quantities of complex and largely unrelated data sets and find exploitable connections and produce useful insights into a deeper meaning in a reasonable amount of time. (Data Link Layer) Top |
|
|
DHCP (Dynamic Host Configuration Protocol) |
| A TCP/IP protocol for assigning IP addresses and related settings to clients on a temporary or permanent basis. Windows clients are set to seek a lease from a DHCP server by selecting “Obtain an IP Address Automatically” in a network adapter’s IP properties dialog. As an alternative, technicians or users can enter static IP settings that do not change until manually altered. (Data Link Layer) Top |
|
|
DNS (Domain Name System) |
| A TCP/IP protocol and general term for the global or enterprise network of systems responsible for resolving fully-qualified domain names (FQDNs) to IP addresses. A domain name is a structured identifier for the zone that contains related devices or devices under a common administration. (Application Layer) Top |
|
|
Driver |
| Software code that allows an operating system to use a piece of hardware by providing logical control. Operating systems are not natively capable of accessing hardware. Drivers specific to both the operating system and the hardware to be controlled act as translators between the two, accepting instructions from the operating system and producing instructions for the hardware and interrupt signals for the BIOS, which is responsible for physical control of the interfaces that lead to the hardware being controlled. (Data Link Layer) Top |
|
|
DSL (Digital Subscriber Line) |
| A broadband internet-access circuit based on a standard pair of phone wires. (Physical Layer) Top |
|
|
E
Encapsulation |
| The addition of control information to a data payload to form a protocol data unit (PDU) that is compatible with the encapsulating technology. Encapsulation is used as a technique for migration from the use of one protocol to a replacement protocol at the same layer, such as from IPv4 to IPv6. It can also be used as a security mechanism to obscure a PDU within another of the same type. (Data Link Layer) Top |
|
|
Encryption |
| The act of altering data to make it unreadable by any person or device, except by the intended recipient, with which a security association has been negotiated, or by an authorized retrieving application. From the perspective of data security, encryption is the primary mechanism for providing confidentiality in stored or transmitted data. (Presentation Layer) Top |
|
|
Ethernet |
| The most common LAN technology in use today. Ethernet, as a Layer-2 protocol, communicates directly with adjacent Layer-3 protocols, such as IP, as well as with the Layer-1 interface electronics that attach to networking media and encode the digital signals passed from above. (Data Link Layer) Top |
|
|
F
Fiber |
| Fiber optics, or optical fiber, refers to the medium and the technology associated with the transmission of information as light pulses along a glass or plastic strand or fiber. Fiber optics is used long-distance and high-performance data networking. (Physical Layer) Top |
|
|
Frame |
| The basic data unit of Layer-2 and some Layer-1 protocols. As a protocol data unit (PDU), a frame is essentially one step above a bit. In fact, a frame is the first data structure above the bit level that gathers bits into a standardized format that is based on the protocol in question. (Data Link Layer) Top |
|
|
FTP |
| Stands for "File Transfer Protocol." FTP is a protocol designed for transferring files over the Internet. Files stored on an FTP server can be accessed using an FTP client, such as a web browser, FTP software program, or a command line interface. (Application Layer) Top |
|
|
FTP (File Transfer Protocol) |
| A TCP/IP protocol for transferring data between a client and server at the file level. FTP uses a pair of TCP ports, 20 and 21, in its insecure form and 989 and 990 with implicit security; the higher numbered port in each case is used to create, maintain, and then tear down the session while the lower one is used for the transfer of data. The term FTP is also often used loosely to refer to a utility that uses the FTP protocol in the background while presenting a graphical user interface (GUI) that resembles two folders—a local one and one representing the remote server folder—that allows files and folders to be dragged back and forth between them. (Transport Layer) Top |
|
|
G
Gateway |
| A classic term for a router; a router at the edge of a network or enterprise internet; a multi-layer protocol converter. Before the term router was settled upon, routers were called gateways, which is the source of the still common term “default gateway,” meaning the default router on a subnetwork, used by local hosts when transmitting packets to remote networks not found in their own routing tables. The term gateway eventually came to refer to a system capable of translating each layer of all or a portion of the protocol stack of inbound data to protocols in the corresponding layers of a different stack before transmitting the data out through a different interface. (Network Layer) Top |
|
|
GPS (Global Positioning System) |
| Developed for military use, the worldwide network of satellites used to pinpoint the location and altitude of terrestrial mobile electronics; in general, the access service subscribed to or the devices employed by users of the GPS network. GPS transceivers are built into devices from smartphones and wearable fitness devices to the electronic consoles of land-, air-, and water-faring vehicles, many of which also provide entertainment functions. In addition to location, mapping, and navigation services, GPS is used by receivers for clock synchronization because of the precise atomic clocks that are present in the satellites. (Physical Layer) Top |
|
|
GUI (Graphical User Interface) |
| A computing user interface (UI) characterized by a full-screen work area and icons that represent objects such as folders and files. GUIs work well with pointing-style input devices—mice and trackballs, for instance—because the work area is laid out as a two-dimensional Cartesian grid. (Application Layer) Top |
|
|
H
Host |
| A networked device with an IP address; a mainframe computer system; the operating system on which a hypervisor runs. IP hosts are named after the mainframes of legacy and modern centralized networking environments. (Network Layer) Top |
|
|
HTTP |
| Stands for "Hypertext Transfer Protocol." HTTP is the protocol used to transfer data over the web. It is part of the Internet protocol suite and defines commands and services used for transmitting webpage data. (Application Layer) Top |
|
|
Hub |
| A Layer-1 Ethernet device with multiple network interfaces; in general, the central concentrating device in a star-wired hub-and-spoke topology. The Ethernet hub is essentially a multiport repeater dealing only with regenerating inbound signals before sending them out all ports simultaneously. As the generic center of a star-wired topology, the hub device can be a hub, switch, concentrator, router, or a multifunction device offering a combination of such functions. (Physical Layer) Top |
|
|
I
ICMP |
| Stands for "Internet Control Message Protocol." When information is transferred over the Internet, computer systems send and receive data using the TCP/IP protocol. If there is a problem with the connection, error and status messages regarding the connection are sent using ICMP, which is part of the Internet protocol. (Network Layer) Top |
|
|
IGMP |
| nternet Group Management Protocol (IGMP; Defined in RFC 1112) is a protocol that allows a host to advertise its multicast group membership to neighboring switches and routers. IGMP is a standard protocol used by the TCP/IP protocol suite to achieve dynamic multicasting. (Network Layer) Top |
|
|
IMAP |
| In computing, the Internet Message Access Protocol (IMAP) is an Internet standard protocol used by email clients to retrieve email messages from a mail server over a TCP/IP connection. IMAP is defined by RFC 3501. (Presentation Layer) Top |
|
|
Interface |
| A physical port used for connectivity to a network or peripheral device; a point of interconnection between two cables, two components, two protocols, two software processes, or two networks. Cabling interfaces are often interchangeably referred to as ports. Interfaces between software or protocol objects can also be referred to as ports in a logical sense. The term socket is also used in some cases with the same meaning. (Data Link Layer) Top |
|
|
Internetwork |
| A network of networks. An internetwork, or internet for short, is created when two or more autonomous networks are interconnected, usually with one or more Layer-3 devices in between. For instance, two fully established LANs connected to one another by a single router constitutes a simple internet. The “internet” refers to the global internetwork that exists by virtue of autonomous networks from around the world being interconnected. (Network Layer) Top |
|
|
IPsec (Internet Protocol Security) |
| A framework of protocols designed to secure IP traffic between two endpoints. IPsec creates virtual private networks (VPNs) by comprising protocols that can exchange security keys privately as part of the confidential negotiation of a security association between endpoints joined by an insecure network such as the internet. (Network Layer) Top |
|
|
IPv4 |
| The primary Layer-3 protocol in use on the internet and private intranets. Internet Protocol version 4 (IPv4), like many Layer-3 protocols, provides end-to-end logical identifiers—32-bit IPv4 addresses, represented as four, eight-bit decimal numbers separated by periods (dotted decimal notation), such as 192.168.10.1. IPv4 addresses have a hierarchical address structure that lends itself to routing. (Network Layer) Top |
|
|
IPv6 |
| The Layer-3 protocol designed to replace IPv4. Internet Protocol version 6 (IPv6) features 128-bit addresses that provide 296 times the number of addresses possible with IPv4. Unlike the decimal-based notation used to represent IPv4 addresses, eight fields of four hexadecimal (hex, for short) digits—a total of 32— are used to represent IPv6 addresses. An example IPv6 address is 2001:0db8:1234:5678:02ab:cdff:feef:1234. (Network Layer) Top |
|
|
IRC |
| Stands for "Internet Relay Chat." IRC is a service that allows people to chat with each other online. It operates on a client/server model where individuals use a client program to connect to an IRC server. Popular IRC clients include mIRC for Windows and Textual for OS X. Several web-based clients are also available, including KiwiIRC and Mibbit. (Application Layer) Top |
|
|
ISDN (Integrated Services Digital Network) |
| A collection of lower-layer protocols and related circuits often used for broadband internet access. ISDN is named for its all-digital support of voice, data, and video services. (Physical Layer) Top |
|
|
J
Jitter |
| Variation in the latency (delay) on a network. Although delay can be tolerated in real-time connections at significant levels, a small amount of jitter can greatly disrupt such a connection. Proper buffering can mitigate the effects of reasonable jitter, but considerable jitter will underrun the buffer and cause degradation. (Data Link Layer) Top |
|
|
JPEG |
| Stands for "Joint Photographic Experts Group." JPEG is a popular image file format. It is commonly used by digital cameras to store photos since it supports 224 or 16,777,216 colors. The format also supports varying levels of compression, which makes it ideal for web graphics. (Presentation Layer) Top |
|
|
L
LAN (Local Area Network) |
| A network that is fully owned by an enterprise; a network that geographically spans a small area, such as a building or floor; a network consisting of all devices behind and including a single router interface; a network that uses a class of Layer-2 protocols limited to deployment on a LAN. (Physical Layer) Top |
|
|
Latency |
| The amount of delay in a communication pathway. For non-real time traffic, latency is not a concern until the delay is so extensive that the application responsible for the data transmitted fails as it waits for a response from the opposing end. With real-time traffic, latency has a more noticeable effect. Nevertheless, users generally do not perceive a roundtrip latency less than 250ms in VoIP networks. (Data Link Layer) Top |
|
|
Load balancing |
| Sending proportionate data traffic across multiple signal pathways. The term load balancing is often used interchangeably with load sharing. However, load sharing can technically be achieved simply by using multiple pathways to send data in the same general direction, but load balancing seeks to adjust shared loads based on a criterion, up to and including maximizing throughput per pathway. (Presentation Layer) Top |
|
|
M
Man-in-the-Middle Attack (MITM) |
| Any of a family of cyber-attacks characterized by insinuating the attacking system between two legitimately communicating systems. MITM attacks can be perpetrated to steal information or influence the flow of information. Attackers can eavesdrop passively or masquerade as one or both compromised endpoints. (Data Link Layer) Top |
|
|
Mirroring |
| Configuring an interface on an Ethernet switch to forward frames intended for all other interfaces. Normally, Layer-2 Ethernet switches will forward only unknown traffic and traffic intended for the device attached to a particular port. (Data Link Layer) Top |
|
|
Modem (modulator/demodulator) |
| A data communications equipment (DCE) device that assists a data terminal equipment (DTE) device, such as a personal computer, in communicating across a wide-area link. (Physical Layer) Top |
|
|
MPEG |
| Stands for "Moving Picture Experts Group." MPEG is an organization that develops standards for encoding digital audio and video. It works with the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) to ensure media compression standards are widely adopted and universally available. (Presentation Layer) Top |
|
|
Multiplexing |
| The combining of multiple sources of data traffic onto a single communications pathway. Multiplexing is also used to describe the process of interleaving the traffic of all transmitting or receiving applications across the same bitstream down through the protocol stack and across the network media. (Transport Layer) Top |
|
|
N
Node |
| Any active device anywhere in a network. Node is a generic term that comes in handy whenever the speaker or writer needs a term that does not commit to a function. On occasion, “node” is used in place of the term host as an adjective to mean “related to one of the devices on an IP network,” as in “node ID” in place of “host ID.” (Physical Layer) Top |
|
|
O
Optical fiber |
| A type of cabling media that guides light waves down a core made of glass or plastic. Fiber optic cable is categorized into two primary types: multimode (MMF) and single-mode (SMF). MMF is used primarily for LAN implementations, where distances are shorter than those found in the wide area, an application best suited for SMF. (Physical Layer) Top |
|
|
OSPF (Open Shortest Path First) |
| A link-state routing protocol that supports large private internetworks. OSPF is ideal for large enterprise networks when it is deployed as intended by establishing hierarchically addressed regions known as areas. (Transport Layer) Top |
|
|
P
Packet switched network |
| A network characterized by constantly variable pathways, created on demand or permanently established, through a group of switches. Unlike with circuit-switched networks, packet-switched networks require each frame of information sent have its own independent addressing information that can be used by the switching devices to forward the frame over an arbitrarily chosen pathway. Because the pathway can change from frame to frame, packet-switched networks require that the more expensive circuit emulation be used or that the user subscribes to a circuit-switched network instead. (Network Layer) Top |
|
|
Packet |
| The data structure often associated with Layer-3 protocols. It is common to refer to an IP datagram as an IP packet. Packets are often only a portion of an entire application message that has been broken into smaller pieces to fit within the smaller limits imposed by lower-layer data structures, such as frames. (Network Layer) Top |
|
|
Ping |
| The act of, or the utility used in, testing the availability of a remote IP host. The Internet Control Message Protocol (ICMP) is used by the ping utility to send an echo request to the remote host in question. The expectation is that an echo reply will be returned by the remote host, indicating that it is powered on and operational. If no reply is received, more troubleshooting must be performed because only a successful ping provides definitive information. (Network Layer) Top |
|
|
Port |
| A physical interface on an electronic device; a differentiating logical identifier for an application or process. When used to refer to logical software identifiers, the term port often appears in discussions of the TCP/IP Transport-layer protocols TCP and UDP. Both protocols dedicate the first two fields in their headers to the source and destination numeric identifiers of the processes that they encapsulate. Common port numbers should eventually be recognized by network and security professionals because they are used in the configuration of firewalls and end devices to specify which processes should be allowed or denied access beyond the point of configuration. (Transport Layer) Top |
|
|
PPP |
| Stands for "Point-to-Point Protocol." PPP is a protocol that enables communication and data transfer between two points or "nodes." For many years, PPP was the standard way to establish a dial-up connection to an ISPs. As dial-up modems were superseded by broadband devices, PPP connections became increasing. However, PPP lives on in "PPP over Ethernet" (PPPoE), which is a common way to connect to the Internet using a DSL modem. (Data Link Layer) Top |
|
|
Protocol |
| An agreed upon method for communication; a set of rules for communication. Data protocols serve to standardize how endpoints and intermediate devices interoperate. Without one or more common protocols, two end devices fail to be able to communicate with one another. (Transport Layer) Top |
|
|
Proxy server |
| An edge device that acts on behalf of other devices. Proxy servers provide multiple functions and are generally positioned in such a way that all outbound traffic must pass through the server. This positioning supports most of the server’s roles, such as permitting or denying different types of outbound traffic generated by clients within the intranet and caching received web content as clients request it. (Application Layer) Top |
|
|
Public key cryptography |
| The use of a related public and private pair of cryptographic keys for authentication, confidentiality, or both. When the keys are generated along with a certificate by a trusted certificate authority (CA), their use is said to be a part of a public key infrastructure (PKI). PKI all but eliminates the possibility of a third party’s compromising the private key. The basis for the cryptography is that neither key can decrypt what it has encrypted. It takes the opposing key to do so. (Transport Layer) Top |
|
|
R
Router |
| A Layer-3 device used in forwarding traffic from one logical segment to another to send the traffic toward the intended recipient. In TCP/IP internetworks, routers are used to forward IP traffic based on reachability information stored in the router’s routing table. (Network Layer) Top |
|
|
Routing protocol |
| A protocol that helps to build a routing table. In addition to dynamic routing protocols, such as OSPF, EIGRP, RIP, IS-IS, and BGP, you can consider the configuration of static routes and configuring IP addresses on a device’s networking interfaces to be routing protocols in that the syntax involved in these configurations is an agreed-upon set of rules, as are all protocols. (Network Layer) Top |
|
|
Routing table |
| A database of known network and host destinations from the perspective of the device that uses it. Each entry in a routing table contains, at a minimum, the destination to be reached, a subnet mask to allow comparison of the destination address in an IP header to the relevant portion of the destination in the table’s entry, an interface to exit through to get to the destination or to the next router in the path, the IP address of the next device to pass the packet to, and a metric to act as a final tie-breaker should there be two entries that match the intended destination. Should there be multiple matches with no way to decide which is best, the default behavior of most routers is to use up to the maximum number of paths allowed simultaneously, increasing overall available bandwidth. (Network Layer) Top |
|
|
S
Single Sign-On (SSO) |
| An authentication model in which only one set of login credentials is required to gain access to many systems. (Presentation Layer) Top |
|
|
Sockets |
| When a computer program needs to connect to a local or wide area network such as the Internet, it uses a software component called a socket. The socket opens the network connection for the program, allowing data to be read and written over the network. It is important to note that these sockets are software, not hardware, like a wall socket. So, yes, you have a much greater chance of being shocked by a wall socket than by a networking socket. (Session Layer) Top |
|
|
Spanning Tree Protocol (STP) |
| A bridging and switching protocol designed to prevent broadcast storms in logical segments that contain physical loops. (Data Link Layer) Top |
|
|
Spooling |
| Storing content to be printed in a buffer held in RAM or on a drive until the printer is ready to process the print job. Print spoolers can exist in the printer, in the server to which the printer is attached, and in the host that originally generated the print job. Using a spooler allows the host to continue with other processing while the printer becomes ready to receive the print job. (Presentation Layer) Top |
|
|
SSH |
| Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Typical applications include remote command-line, login, and remote command execution, but any network service can be secured with SSH. (Application Layer) Top |
|
|
Subnetting |
| The act of splitting a larger IP address space into smaller broadcast domains known as subnetworks or subnets (not to be confused with subnet masks, or masks for short). Subnetting is especially necessary with IPv4 to save precious address blocks by splitting them into more appropriately sized segments based on the expected number of hosts present on a given subnet and on any potential future growth of that subnet. (Network Layer) Top |
|
|
Switch |
| A Layer-2 device that forwards, filters, or floods frames based on the destination address in the header of the frame. Ethernet switches maintain a table that consists of the physical interfaces on the switch associated with the MAC addresses that have been learned by the switch through inspection of the source addresses in the headers received on the associated ports. Switches are not authorized to discard unknown traffic and must therefore flood it. (Data Link Layer) Top |
|
|
T
T1 (also written T-1) |
| One of a class of digital terrestrial circuits that consists of 24 distinct time-division multiplexed channels and a bitrate of 1.544Mbps. The T1 circuit carries a signal known as Digital Signal Level 1 (DS-1). Each of the 24 channels consists of a 64kbps signal known as a DS-0. T1s, in turn, are gathered into groups of 28 to form a DS-3 signal that is transmitted over a T3 circuit at a rate of 44.736Mbps. T1 circuits were once extremely popular dedicated leased telco lines because dedicated bandwidth results in a much better sustained performance when compared to shared circuits of considerably greater bandwidth. (Physical Layer) Top |
|
|
TCP (Transmission Control Protocol) |
| The primary Layer-4 protocol in the TCP/IP protocol suite. Along with UDP, TCP is one of two transport protocols responsible for carrying the traffic from higher-layer sessions across an internetwork. TCP is considered a reliable, connection-oriented protocol because a virtual circuit must be negotiated and established before data will begin to flow between the connection endpoints (connection-orientation) and because TCP acknowledges receipt of data (reliability). (Transport Layer) Top |
|
|
TCP/IP (Transmission Control Protocol/Internet Protocol) |
| The principal protocol suite in use in the industry today. TCP/IP is the protocol suite used on the internet. The suite consists of easily thousands of individual protocols, of which TCP and IP are only two but the most prominent two. As a protocol model, TCP/IP comprises four distinct layers, three fewer than the OSI Model because TCP/IP specifies application protocols that perform the tasks of the top three layers of the OSI Model, and the bottom two layers of the OSI model are not in the purview of TCP/IP but are relegated instead to the network adapter, such as an Ethernet NIC. (Transport Layer) Top |
|
|
Transceiver |
| A portmanteau for transmitter/receiver that refers to a circuit that transmits outbound traffic to and receives inbound traffic from a network. Transceivers also act as converters that turn the type of digital signal in the computer and network card into the type of digital signal that is compatible with the network media. (Physical Layer) Top |
|
|
Twisted-pair cable |
| The primary form of copper cable used in modern star-wired networks. Unshielded twisted-pair (UTP) is the wiring standard recommended for structured cabling installations. (Physical Layer) Top |
|
|
U
UDP (User Datagram Protocol) |
| Along with TCP, one of the two Layer-4 transport protocols in the TCP/IP suite. UDP is an unreliable, connectionless protocol in that it offers best-effort delivery with no guarantees of arrival or flow control. (Transport Layer) Top |
|
|
C
Vable modem |
| The customer premise equipment (CPE) used to send and receive internet traffic over a coaxial cable television circuit. Cable modems use a technology known as DOCSIS (Data Over Cable Service Interface Specification) to encode the data traffic for transmission onto the broadband cable TV network and decode such signals as they are received. (Data Link Layer) Top |
|
|
V
Virtual LAN (VLAN) |
| A broadcast domain created through configuration on a Layer-2 switch. All interfaces on the switch that are placed in the same VLAN are part of the same broadcast domain. A router is required to allow communication from one broadcast domain to another. The value of VLANs stems from the ability to create security domains separated by routers without the need to position devices together in the same area of the enterprise. (Data Link Layer) Top |
|
|
Virtual Private Network (VPN) |
| A network created by encrypting traffic between two endpoints that are connected to one another across an insecure network, such as the internet. Security and tunneling protocols, including IPsec and L2TP, are used to create a secure channel for all traffic to traverse. VPNs can also be created higher in the protocol stack using SSL and TLS. (Data Link Layer) Top |
|
|
Voice over Internet Protocol (VoIP) |
| A framework of protocols that enables two or more IP hosts, usually IP phones, to digitize and packetize analog voice signals and transmit them to one another. VoIP implementations use call setup protocols for a voice gateway (voice-enabled router) to signal to a gateway controller (a server) that one party would like to call another. (Transport Layer) Top |
|
|
W
Wavelength |
| The property of analog and digital signals found by measuring the distance between where one wave begins and where the subsequent wave begins. Wavelength is inversely proportional to frequency, which is the measure of time that it takes for one wave to complete but is calculated as the number of waves that are transmitted in the space of one second. Therefore, if more waves can be transmitted per unit of time (higher frequency), then the distance spanned by each wave must be less (shorter wavelength). (Physical Layer) Top |
|
|
Wide Area Network (WAN) |
| A network that is leased from a service provider; a network that geographically spans a large area, such as between cities or around the world; a network spanning a great distance between two router interfaces; a network that uses a class of Layer-2 protocols positioned for deployment on a WAN. Technically, WAN and internetwork are not interchangeable terms, but many in the industry, including experts, seem to believe that they are. WAN links have a recurring fee that must be paid under pain of cancellation. (Data Link Layer) Top |
|
|
Wi-Fi |
| The term used by the Wi-Fi Alliance to refer to the technology that the IEEE calls 802.11. There are five protocols in the Wi-Fi family that have enjoyed a respectable amount of support: 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac. (Physical Layer) Top |
|
|
Winsock |
| Winsock is actually short "Windows sockets," which are files that allow Windows programs to connect to the Internet and other computers. Technically, Winsock is an "Application Programming Interface (API)," that developers use to make their programs network-enabled. 16-bit applications use a file called WINSOCK.DLL and 32-bit applications use a file called WSOCK32.DLL. Both of these files are libraries of networking functions (based on TCP/IP), but they can differ from computer to computer, depending on the vendor. (Session Layer) Top |
|
|
Wireless Access Point (WAP) |
| A concentrating device for wireless networks. WAPs create a wireless infrastructure and often provide connectivity to the wired infrastructure as well. Because both wired and wireless clients share the same IP subnet, the WAP plays the role of translational bridge (xBr), converting between 802.11 and 802.3 media access methods and frame formats. Providing routing functionality in the same situation would work for the protocol conversion but not for keeping all clients on the same subnet. (Physical Layer) Top |
|
|
Wireless security |
| A group of protocols that are used for authentication and to secure wireless LANs (WLANs) to varying levels. Security for WLANs also includes not broadcasting the SSID, or name of the network, and keeping a list of MAC addresses to filter based on allowed or denied wireless supplicants. (Data Link Layer) Top |
|
|
Wireless |
| A form of node connectivity that replaces cables with radio waves or invisible wavelengths of light. (Physical Layer) Top |
|
|